- Anyconnect Webvpn Web
- Webvpn Anyconnect Enable
- Anyconnect Webvpn Login
- Anyconnect Webvpn Windows 10 Issue
- Cisco Anyconnect Webvpn
- Anyconnect Webvpn Download
Cisco WebVPN Disconnect 1. To connect, right-click on the Cisco AnyConnect icon in the system tray 2. The VPN widnow opens, type connect.uiwtx.edu under the address filed and click Connect 3. Under the fallowing window, type the same username and password used to UIW email 4.Once correct credentials are provided the connected window will show. Secure VPN access for remote workers Cisco AnyConnect Secure Mobility Client empowers remote workers with frictionless, highly secure access to the enterprise network from any device, at any time, in any location while protecting the organization.
The final way of connecting to an ASA with SSL is thick or full client. This client provide us with all functionality that traditional Cisco client does with few benefits, such as the fact that we don’t have to install a client on all PCs in order to allow them to connect to our HQ. We connect to our SSL portal, authenticate and then AnyConnect is automatically downloaded and installed or we are given the option to install it and run it. After the session is terminated, AnyConnect client can remain installed on a client PC or can be removed, depending on how we set up our ASA. One more advantage over traditional IPSec client that we can easily upgrade AnyConnect on all client PCs.
First step is obtaining AnyConnect image from a Cisco site. We need CCO for this. Be aware not to download a .MSI package because this package is used for installing directly on a PC. Rather we download a .PKG file and place it on a TFTP server and download it on our ASA box:
copy tftp://10.x.y.215/anyconnect-win-2.5.6005-k9.pkg disk0:
Address or name of remote host [10.x.y.215]?
Source filename [anyconnect-win-2.5.6005-k9.pkg]?
Destination filename [anyconnect-win-2.5.6005-k9.pkg]?
Accessing tftp://10.x.y.215/anyconnect-win-2.5.6005-k9.pkg…!!!!!! <many more of these deleted>
Writing file disk0:/anyconnect-win-2.5.6005-k9.pkg…
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! <many more of these deleted>
4929918 bytes copied in 6.530 secs (821653 bytes/sec)
Now we need to tell ASA which image to use and in what order, because we may have more than one version on ASAs flash. We also need to explicitelly enable AnyConnect, web VPN itself and allow users to select a group membership:
Anyconnect Webvpn Web
webvpn
svc image disk0:/anyconnect-win-2.5.6005-k9.pkg
svc enable
enable outside
tunnel-group-list enable
exit
Webvpn Anyconnect Enable
After we do this, the ASA will unpack this package into this location in the RAM: cache:stc/1. If we had more than one image, for different operating systems and versions, there would be cache:stc/2, cache:stc/3, …
If you are curious what is there:
ASA-TEST(config-webvpn)#
ASA-TEST(config-webvpn)# dir cache:stc/1
Directory of cache:stc/1/
0 -rw- 0 21:36:56 Jul 30 2012 Windows
0 -rw- 513 21:36:56 Jul 30 2012 VPNManifest.xml
0 -rw- 8419 21:36:56 Jul 30 2012 tips.htm
0 -rw- 3279 21:36:56 Jul 30 2012 strings.js
0 drwx 0 21:36:56 Jul 30 2012 locale
0 -rw- 7931 21:36:56 Jul 30 2012 index.html
0 drwx 0 21:36:56 Jul 30 2012 images
0 -rw- 18 21:36:56 Jul 30 2012 headinfo.txt
0 -rw- 134 21:36:56 Jul 30 2012 empty.html
0 drwx 0 21:36:56 Jul 30 2012 binaries
0 -rw- 90965 21:36:56 Jul 30 2012 AnyConnectProfile.xsd
4960256 bytes total (2142087168 bytes free)
ASA-TEST(config-webvpn)#
One thing is worth noting now. The ASA code after 8.3 used “anyconnect” keyword instead of “svc” in previous example. So, for instance, if we were to run this code, the example from above would be:
webvpn
anyconnect image disk0:/anyconnect-win-2.5.6005-k9.pkg
anyconnect enable
exit
Other things should be pretty much the same.
So far we didn’t need an IP address pool for SSL clients, but now we do, so let’s create one:
ip local pool Pool1 10.49.49.128-10.49.49.254 mask 255.255.255.128
Now we need a tunnel group and a group policy for our users, connect the two and set up basic parameters:
group-policy ADMINS internal
group-policy ADMINS attributes
vpn-tunnel-protocol svc
tunnel-group ADMINS type remote-access
tunnel-group ADMINS general-attributes
address-pool Pool1
default-group-policy ADMINS
tunnel-group ADMINS webvpn-attributes
group-alias ADMINS enable
This is the basic Anyconnect setup that will allow a user to authenticate and automatically download and start Anyconnect. A few more steps are required or desirable in order for everything to work…
Anyconnect Webvpn Login
What we have done so far allows us to log on using only LOCAL database (which is by default, because we did not specify anything), so we need at least one user. We will give him/her a password and an attribute which will only allow a remote VPN session, not a console access to the box:
username sasa pass spop123
username sasa attributes
service-type remote-access
This ASA is set up for basic outbound access with PPPoE/ADSL, like described at the beginning of EzVPN Remote with ASA5505 article. In order to allow Anyconnect users to access HQ resources, we need two more things: one is NAT and the other is permitting this traffic with ACL. First NAT:

object network NETWORK_VPN_10.49.49.0_SLASH128
subnet 10.49.49.128 255.255.255.128
nat (inside,outside) source static any any destination static NETWORK_VPN_10.49.49.0_SLASH128 NETWORK_VPN_10.49.49.0_SLASH128
First command creates a NAT object that corresponds to VPN address pool created previously, and the second command (which needs to be entered in a single line) does the actual NAT. This 8.3 style NAT and I will deal with it in some future article(s).

The other thing is permitting the traffic in. We can do that with plain old simple ACL or we could use:
sysopt connection permit-vpn
which will actually permit all VPN traffic in.
Now we have a perfectly working AnyConnect example. After we connect to a WebVPN portal and log in, we will automatically download and install Anyconnect. After that, we will switch from a webvpn to an anyconnect session, receive an IP address and start passing encrypted traffic to our HQ. After we disconnect, Anyconnect will remain installed on our PC.
Anyconnect Webvpn Windows 10 Issue
Although we can tweak many things regarding WebVPN, at the end of this blog we will set up our ASA for split tunneling. What this means is that we will not send all traffic to HQ but only some networks, the ones described in an access list. All other traffic will be sent via our default gateway to the Internet. Here is how this is done.
First we create an access list to state what subnets we want to encrypt. We could use a standard ACL:
access-list ST_HQ standard permit 192.168.192.0 255.255.255.0
The interpretation of this ACL is simple: please encrypt all traffic for 192.168.192.0/24 network and nothing else. We could specify as many networks as we want.
Cisco Anyconnect Webvpn
After we stated what we would like to encrypt, we need to tell the ASA about it:
group-policy ADMINS attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ST_HQ
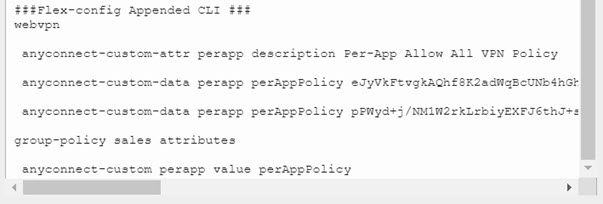
Anyconnect Webvpn Download
And that’s it! We can verify in the Anyconnect client that we indeed only encrypt selected traffic:
This article concludes our ASA WebVPN saga. For now. I will try to blog a little bit more on this topic on ASA and IOS as well in some future blogs.
